NGINX Integration Guide
AppSentinels supports NGINX integration through lightweight, linkable modules or plugins that can be incorporated into your existing web server deployments.
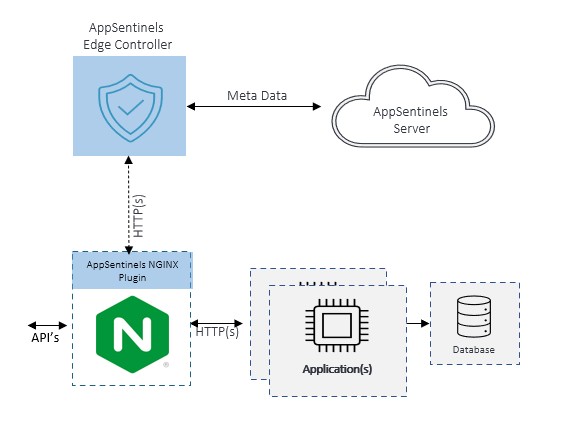
- Traffic Processing: AppSentinels NGINX modules intercept HTTP traffic and forward log data to the AppSentinels Edge Controller for security analysis.
-
Two Modes Supported: Modules operate in two modes:
- Out-of-Band (OOB) / Transparent Mode
- Service-Chaining / Enforcement Mode
- Transparent Mode: The plugin simultaneously forwards the request to both the application and the Edge Controller. This ensures the application continues processing while logs are asynchronously analyzed.
- Enforcement Mode: The plugin first sends the request to the Edge Controller. Based on the controller’s response, it then forwards or blocks the request, enabling inline enforcement of security decisions.
-
Fail-Open Safety: In enforcement mode, a
max-latencyconfiguration ensures high availability. If the Edge Controller does not respond within the defined latency threshold, the plugin enters fail-open mode and forwards the request directly to the application.
🚀 Deployment Options
AppSentinels provides flexible deployment options to suit different infrastructure setups. You can integrate the modules into either host-based (baremetal) NGINX or container-based NGINX deployments.
NGINX or NGINX Running on Host - This option is suitable for environments where NGINX is installed directly on the host operating system (e.g., VM, physical server).
Container-Based NGINX Deployments - This option is intended for modern environments using Docker or container orchestration platforms like Kubernetes.
Baremetal NGINX or NGINX Running on Host
AppSentinels provides two loadable modules to be used with your existing host-based NGINX deployment:
nginx_ext_auth_module.songinx_ext_access_log_module.so
These modules must be properly loaded and configured as explained in the steps below.
1. Load Modules
-
Copy Modules: Copy or mount the modules to a
directory accessible by NGINX (e.g.,
/etc/nginx/modules/). -
Edit Configuration: Add the following directives
at the global level of nginx configuration
(
/etc/nginx/nginx.conf):
load_module /etc/nginx/modules/nginx_ext_auth_module.so;
load_module /etc/nginx/modules/nginx_ext_access_log_module.so;
thread_pool ext_access_log_thread_pool threads=1 max_queue=10000;
thread_pool ext_monitoring_thread_pool threads=1 max_queue=10;
After editing, restart NGINX to apply the changes and verify the modules are loaded correctly.
2. Configure the Application Server and Location Blocks
2.1 Out-of-Band (OOB) / Transparent Mode
Identify the application you wish to onboard and add the following configuration block into its NGINX server context:
http {
server {
listen 9000;
server_name front-service;
# AppSentinels config block start
ext_auth_log_server http://onprem-controller:9004;
ext_stats_server http://onprem-controller:9004;
ext_instance "uat-region1";
# AppSentinels config block end
location / {
proxy_pass http://localhost:3000;
}
}
}- Ensure the Edge Controller is reachable at the configured URLs.
-
For secure logging over HTTPS, change the scheme from
httptohttpsand confirm that the controller is configured for HTTPS. -
Set a clear and unique
ext_instancevalue for better observability (e.g.,uat-region1). - Restart NGINX to apply the changes.
🔗 View Sample Transparent Mode NGINX Config
2.2 Service-Chaining / Enforcement Mode
Use this mode if inline enforcement is required. The incoming request is validated by the Edge Controller before being forwarded to the application.
server {
listen 9000;
server_name front-service;
# AppSentinels config block start
ext_auth_fail_allow on;
location /auth {
internal;
proxy_pass http://onprem-controller:9004;
}
ext_stats_server http://onprem-controller:9004;
ext_instance "uat-region1";
# AppSentinels config block end
location / {
# AppSentinels config block start
ext_auth_request /auth;
# AppSentinels config block end
proxy_pass http://localhost:3000;
}
}-
Ensure the Edge Controller is reachable via the configured
/authendpoint. -
Set the
ext_instancevalue appropriately (e.g.,uat-region1). - Restart NGINX to apply the changes.
Container-Based NGINX Deployments
The integration approach used for baremetal deployments is equally applicable when NGINX is deployed as a container. AppSentinels modules can be mounted into or bundled within your container images.
1. Load Modules
- Mounting Modules: Mount the AppSentinels modules into the container using volume mounts, or package them into a custom container image.
-
The example below demonstrates mounting modules using
docker-compose. The modules are placed under:/usr/local/openresty/nginx/modules/
openresty:
image: openresty/openresty:alpine
container_name: openresty
ports:
- 7001:7001
- 9000:9000
extra_hosts:
- "onprem-controller:172.17.0.1"
volumes:
- ./nginx_ext_auth_module.so:/usr/local/openresty/nginx/modules/nginx_ext_auth_module.so
- ./nginx_ext_access_log_module.so:/usr/local/openresty/nginx/modules/nginx_ext_access_log_module.so
- ./openresty/nginx.conf:/usr/local/openresty/nginx/conf/nginx.conf
- ./openresty/http.conf:/etc/nginx/conf.d/http.conf🔗 View docker-compose.yaml reference
-
Edit Configuration: Insert the module loading
directives in
nginx.conf. If the container does not provide hooks for inserting these, modify and remount the config.
load_module /etc/nginx/modules/nginx_ext_auth_module.so;
load_module /etc/nginx/modules/nginx_ext_access_log_module.so;
thread_pool ext_access_log_thread_pool threads=1 max_queue=10000;
thread_pool ext_monitoring_thread_pool threads=1 max_queue=10;
After configuration, restart the NGINX container to ensure modules are properly loaded.
2. Configure the Application Server and Location Blocks
- Integration steps remain the same as in baremetal deployment. Choose the right configuration based on the selected mode (transparent or service-chaining).
- Ensure the Edge Controller is reachable from the container at the configured URL.
- Restart the NGINX container to apply the configuration.
Verify Deployment
Once AppSentinels Edge Controllers are deployed and integrated with NGINX, their status can be verified via the AppSentinels Dashboard.
- Navigate to the System Health page in the AppSentinels Dashboard to confirm that all Controllers are visible and running.
- Generate sample application traffic through the monitored NGINX instance.
- Visit the API Catalogue section of the Dashboard to view the automatically discovered APIs.
Deployment / Debugging
- Deploy Edge Controller: Ensure the Edge Controller container is up and running.
- Verify on Dashboard: Once active, it should be visible under the System Health page of your organization’s AppSentinels dashboard.
-
Validate NGINX → Edge Controller Connectivity: By
default, NGINX forwards logs to port
9006on the Edge Controller. Run the following command on the Edge Controller’s VM to verify packet receipt:
tcpdump -i <ingress device eg: eth0, ens3> -A \\
'port 9006 and (((ip[2:2] - ((ip[0]&0xf)<<2)) - ((tcp[12]&0xf0)>>2)) != 0)' | \\
egrep --line-buffered "^........(GET |HTTP/|POST |HEAD )|^[A-Za-z0-9-]+: " | \\
sed -r 's/^........(GET |HTTP/|POST |HEAD )/\\n\\1/g'-
If you see API requests like
POST /auth, it indicates successful communication from NGINX to the Edge Controller. -
If NGINX logs are being sent to a different port, update the
tcpdumpcommand accordingly. - When the Edge Controller is connected to AppSentinels Cloud, your APIs will be visible in the Dashboard automatically.
<ingress device> with the actual network interface
name on your VM (e.g., eth0, ens3).
Upgrading NGINX Version
If NGINX or OpenResty is upgraded to a newer version, the AppSentinels modules must be recompiled for compatibility with the updated binaries.
To initiate the recompilation process, please share the full output of the following system-level commands from the upgraded environment:
- cat /etc/os-release: Provides OS version details
- nginx -V: (capital V) Reveals the exact NGINX build options and version
Once the updated modules are provided by AppSentinels, you can proceed with the integration and restart NGINX or your container as needed.